Data Acquisition 8 | Internet Cookies
Data Acquisition 8 | Internet Cookies

- What is Cookie?
Some people believe the name for internet cookies came from the fairy tale about two children called Hansel and Gretel. The children were able to mark their trail through a dark forest by dropping “cookie crumbs” behind them so that they could see where they had been. This story paints a nice picture of the ability that internet cookies have to track your activity.
We have to use cookies because HTTP is a stateless protocol. For multiple requests from a browser, the server can not identify all these requests are from the same browser. So cookies are the extra data stored in our browser used for maintaining the communication between the client and the server.
2. Setup a Server Using Cookies
To set up a web server locally or remotely (on AWS) that uses the sample cookies, we can use the following flask script.
The Jinja templates for this script are (remember to put in the templates folder),
Type in,
$ python server.py
to run this code, we go to the port 5000 on your server (mine is 18.222.232.14) to communicate with it. We can use F12 to check that we have no cookies now. We can also go to the setting page of the chrome and check that we have no cookies on this webpage.

On this page, we can freely write anything in the input text box. For example, we can type in,
Hello
and then press Login. Then we are going to be directed to a page that tells us the cookie is set successfully. We can find out that now we have a record of a cookie and this cookie is stored in our browser. Every time we connect to this server, this cookie will be sent to the server to identify who we are.
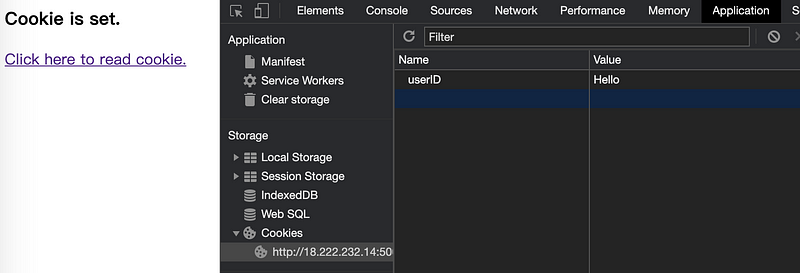
Let’s click on the link to read the cookie.

On this page, the cookie Hello will be sent back to us on the webpage and we can then know what is the cookie that we have set for our browser. Now, if we go to the page of,
<server ip>:5000
The server will know who we are and we do not have to set the cookie for a second time! So the server will redirect us to the /getcookie page.
Now, let’s click on the link that will delete the cookie for this website. Hola! The cookie is now deleted and the server doesn’t know who we are again. We can then re-log to the server for a second time.
3. Cookie Forgery 1: Cheat The Server By Cookies
Because the cookies are stored in our browser, of course, we can also cheat the server by changing the cookie. The server won’t know anything about it! To change the cookie on our browser, we have to use an extension called EditThisCookie. First of all, we have to download this extension and install it on our computer.
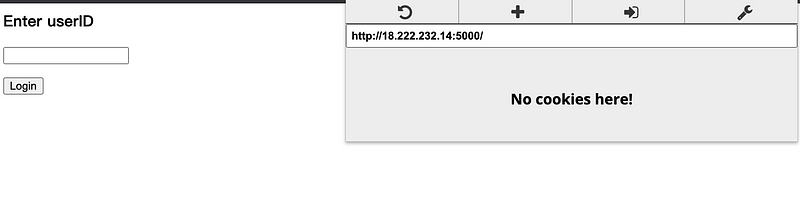
Then we go back to our server. The extension will tell us that there are now no cookies here for this webpage.
Secondly, we enter Hello again and we can find out that Hello is being set for the userID.
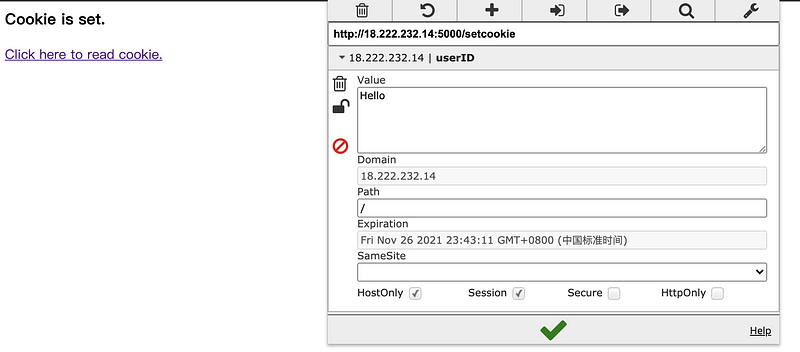
Thirdly, we change the value of the userID to Hi and click on the green √ sign to save this value.
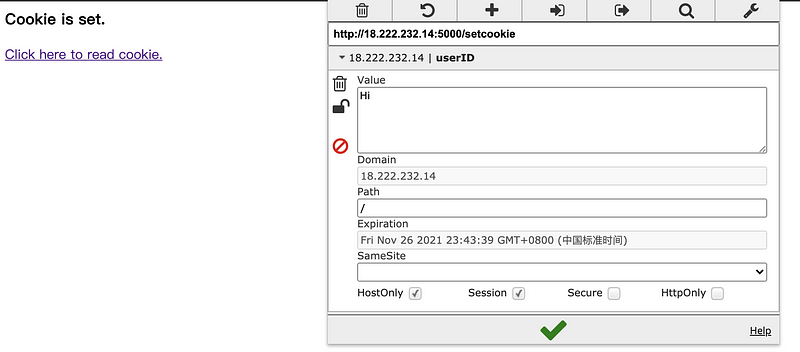
Finally, we click on the link to read the cookie. Then we can find out the userID for us is no longer Hello and we cheated the server and login with the identity of another user.
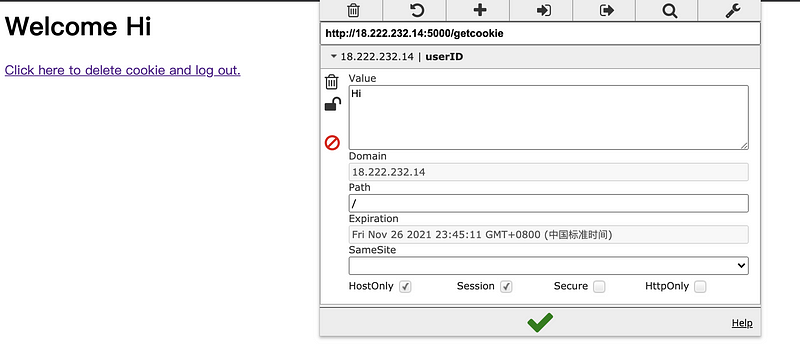
4. Session Cookie
For server developers, they don’t want to store the key information of a user in the browser and there are two reasons. Firstly, the users can change the information and cheat the server (as we have done). Secondly, there can be too many cookies for uploading and it will take forever and not secure if all the cookies with sensitive data are uploaded for every request. That’s why we have the concept of sessions for this.
The sessions are information stored on the server instead of the users’ computer. Well, the user does have a cookie and this cookie always has no specific meaning (it is actually a hash value). For example,
eyJwYXNzd29yZCI6InNkcyIsInVzZXJuYW1lIjoieWltIn0.X7_lSQ.2eR_3gbFtfnnYxoZaT756HJTMUA
However, the server uses this key to identify the users and then calls the information of this specific user from the server.
Again, we run this script and then go to,
<server ip>:5000
For the root page, it is said that we are not logged in. Then we can click on the link to log in.
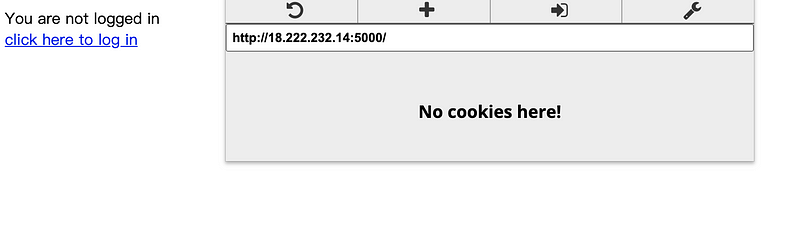
On the login page, it is said that we have to type in the userID and password in order to login. However, this is not a real server so it will not verify the account. We can also discover that there is no cookie at this moment.
Now, let’s randomly type in the userID and the password, for example,
userID: admin
password: admin123pass
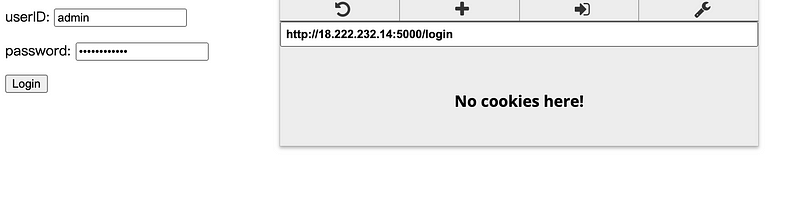
Then we click on the button login to continue.
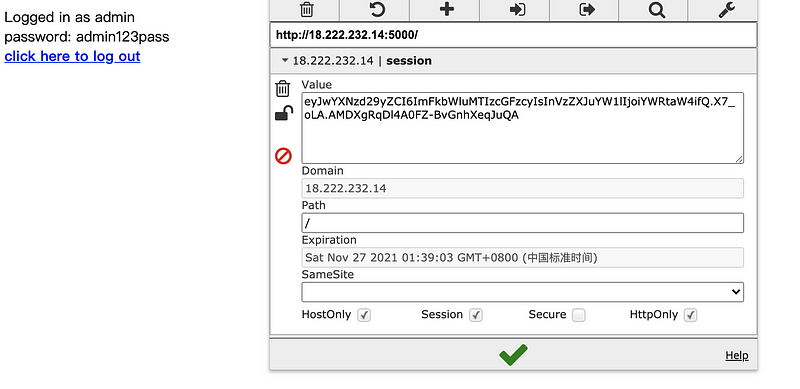
Then we will get a session value (key).
eyJwYXNzd29yZCI6ImFkbWluMTIzcGFzcyIsInVzZXJuYW1lIjoiYWRtaW4ifQ.X7_oLA.AMDXgRqDl4A0FZ-BvGnhXeqJuQA
You can discover that this value is the same as my value. This is because we have the same app.secret_key, the same userID, and the same password, then our hash value for this instance should then be the same.
6. Cookie Forgery 2: Cheat The Server with Session Cookie
Even though it is much safer because if the user doesn’t know the secret key of the server, they can hardly know the meaning of the session value. And the session cookies make it harder for hackers to modify the cookies because there are no sensitive data in the cookie (only the server will know the meaning of these cookies).
However, the cookie session is still not safe because it can be leaked and someone can thus log in with your account. Let’s try this now.
Suppose that I am a client user and I am not the admin. But by some means, I got the admin’s cookie as,
eyJwYXNzd29yZCI6ImFkbWluMTIzcGFzcyIsInVzZXJuYW1lIjoiYWRtaW4ifQ.X7_oLA.AMDXgRqDl4A0FZ-BvGnhXeqJuQA
I firstly log in with my account,
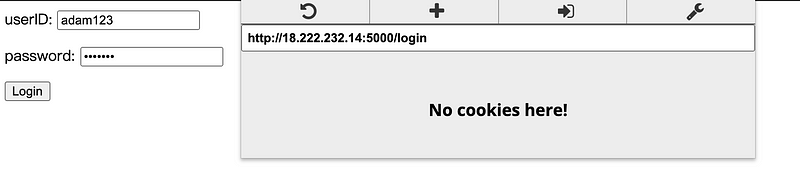
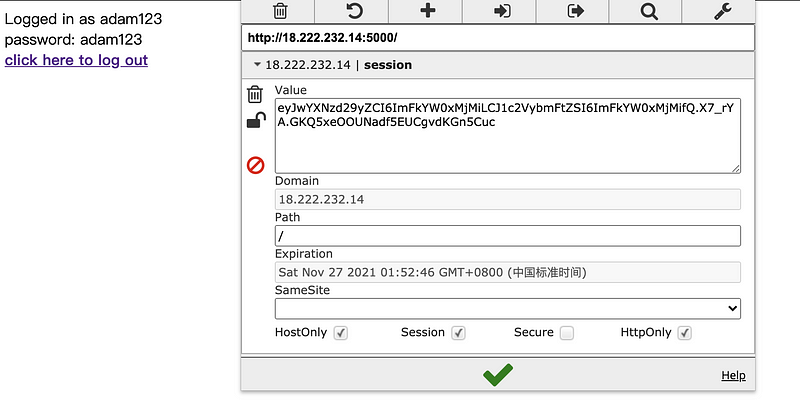
And then change my cookie to the admin’s cookie,
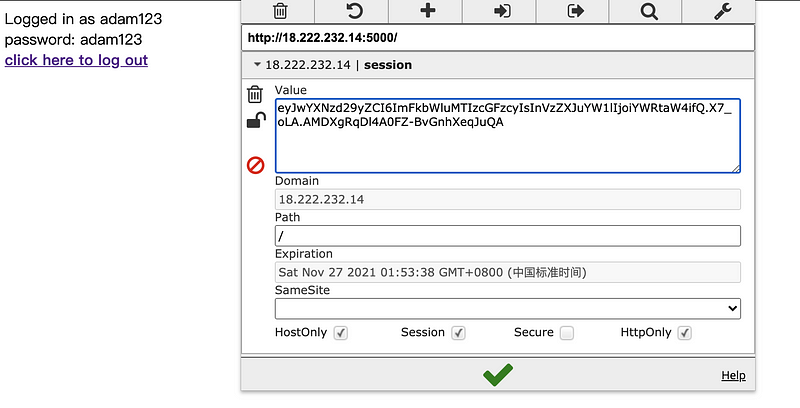
Click on the green √ sign to save this value and then refresh the page.
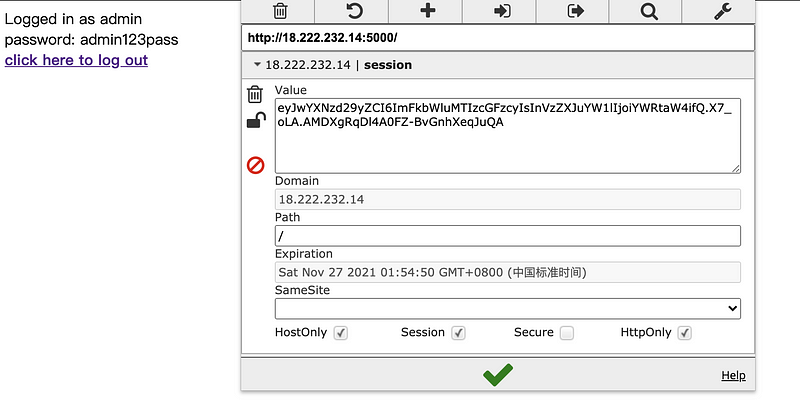
Now we can see the password of the admin. That’s why a leaked cookie value can be really dangerous for us!