Information Security Lab 5 | Disassembly Tools
Information Security Lab 5 | Disassembly Tools

- Ghidra
One of the static analysis tools that we can use for disassembling code is called Ghidra. Ghidra is a free and open-source reverse engineering tool developed by the National Security Agency of the United States of America.
First, let’s download this file from the official website of Ghidra,
$ cd ~/cs6265-tut/
$ curl https://ghidra-sre.org/ghidra_9.2.3_PUBLIC_20210325.zip > ghidra_9.2.3_PUBLIC_20210325.zip
Then, let’s unzip the file and change it to this directory,
$unzipghidra_9.2.3_PUBLIC_20210325.zip
$ cd ghidra_9.2.3_PUBLIC
In this directory, we can change the mode of the file ghidraRun to 777 and then execute this file,
$ chmod 777 ghidraRun
$ ./ghidraRunAfter that, we can choose to set a project directory by “File” -> “New Project”. Select “Non-Shared Project” and specify “Project Name”, and finally drag our local crackme0x00 into the folder just created.
Then let’s double click on this binary to analyze it. To examine the binary, click on main under Symbol Tree. This will take us toward the assembly view of the text segment based on the symbol. Meanwhile, you will have a synced view of the decompiled C code main by Ghidra, side-by-side.
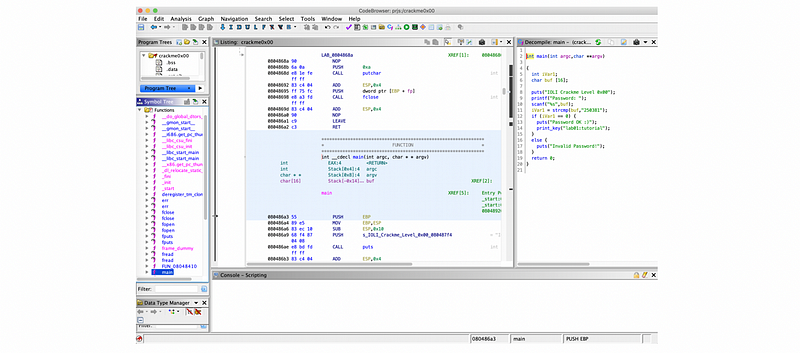
The decompiled C code main code is,
int main(int argc,char **argv)
{
int iVar1;
char buf [16];
puts("IOLI Crackme Level 0x00");
printf("Password: ");
scanf("%s",buf);
iVar1 = strcmp(buf,"250381");
if (iVar1 == 0) {
puts("Password OK :)");
print_key("lab01:tutorial");
}
else {
puts("Invalid Password!");
}
return 0;
}From here, we can clearly see that the password of crackme0x00 should be 250381.
Finally, let’s add a shortcut to Ghidra. First, let’s open .bashrc by vim,
$ vi ~/.bashrc
Then, let’s add new lines in this file,
# alias for ghidra
alias ghidra="~/cs6265-tut/ghidra_9.2.3_PUBLIC/ghidraRun"
Then we save this file and reload the terminal by,
$ source ~/.bashrc
Finally, we can directly open Ghidra by,
$ ghidra
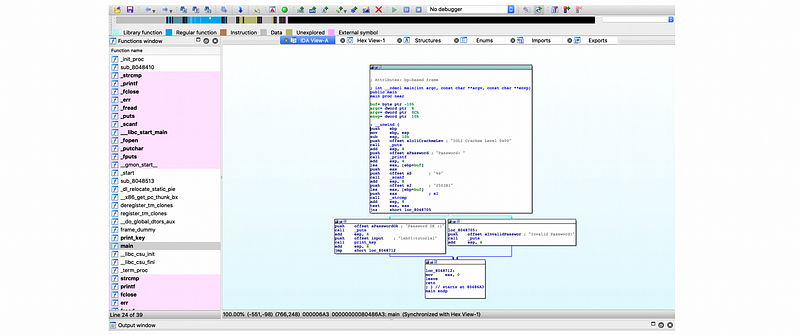
2. IDA
Another software we can use to disassemble a binary is called Interactive Disassembler (aka. IDA). Commonly, we have IDA (for 32-bit address disassembly) and IDA64 (for 64-bit address disassembly) and they are not free. The following tables show the relationship of the logic in the main function. We can also find the password from this analysis.